Podman
Container Technology
Software applications often depend on system libraries, configuration files, or services provided by runtime environments. Traditionally, the operating environment of software applications is installed on a physical host or an operating system running on a virtual machine. System administrators then install application dependencies on the operating system.
Packaging systems such as RPM, which helps administrators manage application dependencies, are available on Red Hat Enterprise Linux. When you install the Apache httpd package, the RPM system also enables the establishment of the right libraries and other dependencies.
The biggest disadvantage of traditionally distributed software applications is that dependencies are mixed with the runtime environment. An application may require older or newer versions of supporting software than the software provided by the operating system. Similarly, two applications on the same system may require different and incompatible versions of the same software. [5]
Packing and distributing applications as a container can help resolve these conflicts. A container is one or more sets of processes isolated from the system. Software containers provide a way for packaging and distribution of applications and facilitate their management.
Consider a container/cargo ship operating for shipping. A shipping container is a standard way to pack and ship goods. It is labeled, loaded, unloaded and transported as a box from one place to another. The contents of the container are isolated from the contents of other containers in such a way that they do not affect each other. These basic principles also apply to software containers.
Red Hat Enterprise Linux supports containers using the following basic technologies:
1. cgroups (control groups): Used to limit access to operating system resources.
2. namespaces: Allows the resources in the system to be isolated in a virtual zone.
3. SELinux (Security-Enhanced Linux): Security module for Linux kernel. Performs permit checks at the operating system level.
Differences Between Containers and Virtual Machines
Containers provide many benefits, such as virtual machines: security, storage, and network isolation. In both technologies, it isolates application libraries and runtime resources from the main operating system or hypervisor, and likewise, the main operating system or hypervisor is isolated from these sources.
Containers and virtual machines interact differently with the hardware and the operating system below it.

Fig. 1. (https://www.atlassian.com/microservices/cloud-computing/containers-vs-vms)
A virtual machine has the following features:
• Allows multiple operating systems to run simultaneously on a single hardware platform.
• Uses a hypervisor to split hardware into multiple virtual hardware systems.
• Requires a complete operating system environment to support the application.
A container has the following features:
• Runs directly on the host OS and shares resources with all containers on the system.
• Shares the core of the host, but isolates application processes from other parts of the system.
• Containers start faster because they require much less hardware resources than virtual machines.
• Includes all dependencies such as system and programming dependencies and configuration settings.
Podman
Podman is an open-source tool and is used to develop, manage and run containers on Linux systems. Originally developed by Red Hat engineers and the open-source community, Podman manages the entire container ecosystem using the libpod library.
Podman's daemon-free and container architecture makes it a more secure and accessible option for container management, and its accompanying tools and features like Buildah and Skopeo allow developers to customize the container environments that best suit their needs.
Podman provides an alternative container engine to Docker for managing containers on Linux systems. There are some key differences between Podman and other container engines like Docker:
1. Podman uses an architecture that does not require a daemon process: An alternative to Docker that requires a daemon process to manage containers, Podman uses an architecture that allows running containers without the need for a separate daemon process. This makes it easier and safer to use, as it eliminates the need for a privileged operation
2. Podman containers are run as regular processes on the host, making them manageable with standard Linux process management tools like systemd or systemctl. This allows it to more easily integrate with existing systems management tools and workflows.
3. With Podman it is possible to run containers as a normal user without the need for root privileges. This makes it easier to secure container environments and users do not need to have root access on the host system.
Overall, Podman provides a lightweight, secure, and flexible way to manage containers on Linux systems, with a focus on ease of use and integration with existing system administration tools.
Podman Setup
It is possible to download Podman in one line. RHEL 9 was used in this study. You can access the installations in other distributions and operating systems from this link.
Ø sudo yum -y install podman

So, as tradition, let's run a Hello-World program first:
Ø podman run quay.io/podman/hello

Podman Container Storage
Each system user has his own container storage space. If you try to capture images from different user sessions, it will take images from the remote record instead of the local image. That is, in cases where different users log in, it states that these users can access their own container storage areas and that the images stored in these storage areas are not available in other users' storage areas. So when a user wants to use an image in their storage area, this image may not be available locally and may need to be downloaded from the remote record.
For example, containers for the root user are stored in directory /var/lib/containers/storage, while for other users it is stored in directory $HOME/.local/share/containers/storage/.
This configuration ensures that each user has access to their own containers and avoids confusion between the containers of different users. For example, an application installed in one user's container may not run in another user's container, or it may be a different version. Therefore, having each user have their own container storage provides a better user experience in the system.
Creating Containers Using Podman
1. First, make sure Podman is installed:
Ø podman --version
![]()
2. Next, a Docker image is downloaded. For example, to download the Nginx web server image, you can use the command:
Ø podman pull nginx

For example, our repository here is docker.io/librariy/nginx. We can choose which repository we want to download with the following command.
Ø podman search nginx

We received a lengthy output. We can find the repository along with its descriptions here. For example, since the repository we used is the official image in the yellow section, we downloaded this image by default.
3. Afterwards, you can use the following command to create a container:
Ø podman run -d –name mynginx -p 8080:80 nginx
![]()
This command creates a container named "mynginx" and forwards port 8080 to port 80. The "-d" option specifies that the container should run in the background. At the end of the command, we specify the name of the image we want to download.
4. To check if the container is running or not, you can use the following command:
Ø Podman ps
![]()
Each line describes information about the container:
CONTAINER ID: Each container receives a unique hexadecimal identifier (ID) when created. This ID, although similar in appearance to an image ID, is unrelated to it.
IMAGE: The IMAGE field specifies the container image used to start the container.
COMMAND: The COMMAND field specifies the command executed when the container is started.
CREATED: The CREATED field displays the date and time when the container was started.
STATUS: The STATUS field shows the total runtime of the container, or if it is still running, the duration, or if it has been terminated, the termination date.
PORTS: The PORTS field specifies the ports that are opened or configured with any port forwarding by the container.
NAMES: The NAMES field specifies the name of the container.
5. You can use this command to test the container. After the private IP address, we accessed it by entering the redirected port.
Ø curl http://172.0.0.62:8080

6. You can use the following command to stop the container:
Ø podman stop mynginx
![]()
7. To delete the container, you can use the following command:
Ø podman rm mynginx
This example scenario demonstrates the process of creating a simple Nginx web server container using Podman. Of course, you can create different scenarios using different images and parameters.
Managing Container Images with Podman
Sometimes, we may need a little assistance, for which we can use the following command:
Ø podman --help | more

Alternatively, you can examine the manual page if it is installed:
Ø man podman

You can also familiarize yourself with the subcommands of Podman for more information:
Ø podman images --help | more

How Does Podman Manage Containers?
Users can pull containers from their own repositories using the Podman CLI. Podman is used to invoke the configured container runtime and, when integrated with systemd, allows for the updating and background execution of containers using systemd services.
Users can automatically start and manage their own containers with their own systemd units. This allows each user to have separate sets of containers and images and enables simultaneous use of Podman on the same host machine. When users are done with their work, they can share their images with others by uploading the changes to a shared repository.
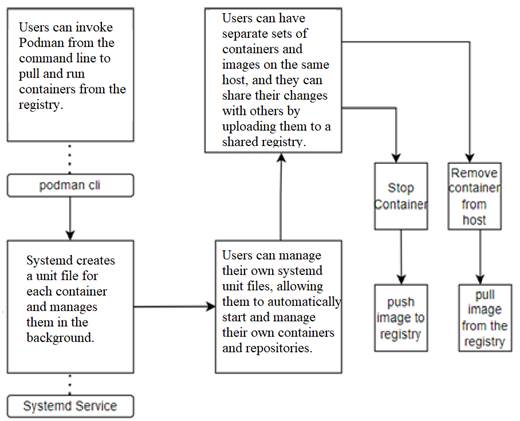
Podman also comes with a RESTful API, allowing calls to Podman from platforms like CURL, Postman, or Google's Advanced REST client to manage containers. This enables users to use Podman with external tools as well.
Initializing the Local Container Image Registry:
The local registry in Podman is a tool that allows you to store and share Podman containers on your local network. It acts as a local registry server and hosts images that can be used to create, run, or stop Podman containers.
The local registry in Podman facilitates the management of hosted and shared images on the local network. This enables sharing images across multiple machines. However, it does not provide a public registry service like Docker Hub; it only serves as a registry for images hosted on your local network.
Using the Podman local registry is straightforward and can be set up in a few steps on your local network. When registering images to the local registry using Podman, you need to assign a tag indicating that the images will be stored in the registry. The default location for this tag is usually localhost:5000, but it can be optionally changed.
Deployment
The easiest way to deploy the registry is by running the following command:
Ø podman container run -dt 5000:5000 --name registry --volume
registry:/var/lib/registry:Z docker.io/library/registry:2

This Podman command creates a Podman container from the docker.io/library/registry:2 image available on Docker Hub. The container is named "registry". Additionally, the container is connected to the /var/lib/registry directory on the host machine as a volume by Podman, and the "Z" option sets the SELinux context of the volume.
The command maps port 5000 to the Podman container's 5000 port, allowing external applications to connect to the Podman container and access a local Docker registry. Therefore, the command creates a Docker registry container to be used as a local Docker registry. The "-d" option runs the container in the background, while the "-t" option creates a TTY connection for the container.
To manage and inspect volumes:
Ø podman volume ls
Ø podman volume inspect registry

As seen, the data will be stored in the home directory, allowing you to restart or even remove the container. If you start a new container and reuse the same volume, you will have access to the already stored images.
Test
To test the functionality, you can download an image and load it into the local registry.
1. Pull the latest ubi8 image from the registry.access.redhat.com registry:
Ø Podman pull registry.access.redhat.com/ubi8/ubi:latest

2. Go to the metadata of a container image:
Ø podman inspect image ubi |more
3. Modifying/Updating labels on existing images:
(Labels are used to provide additional information about images and often include version numbers, creation dates, author information, licenses, etc. Relabeling refers to changing or updating these labels.)
Ø Podman tag ubi:latest localhost:5000/ubi8/ubi

Now we can see the additional label for the UBI image. Note that both have the same image ID value.
4. In the next step, we will load the image into our local registry.
Ø podman push --remove-signatures localhost:5000/ubi8/ubi:latest --tls-verify=false

The "--remove-signatures" option removes signature data from the image before loading it into the registry. This can be used by those who want to bypass security measures, as the registry would normally require a signature key to re-validate the signatures.
Since there is no valid certificate in the test registry, we need to add the "--tls-verify=false" option to our command.
Afterward, you can search in the registry:
Ø podman image search localhost:5000/ --tls-verify=false

5. Now, you can remove your local image and if desired, pull it again from your local registry.
#Remove local image:
Ø Podman rmi registry.access.redhat.com/ubi8/ubi

#Pull the image from the local registry:
Ø podman pull localhost:5000/ubi8/ubi:latest --tls-verify=false

6. If you're done with everything, you can clean up the images, volumes, and containers.
Remove/Delete container
Ø podman container rm -f registry
Remove/Delete volume
Ø podman volume rm registry
Remove/Delete image
Ø podman image rm docker.io/library/registry:2
We can summarize the basic commands as follows:
|
Command |
Description |
|
podman build |
Build a container image from a container file. |
|
|
Run a command in a new container. |
|
|
List images in local storage. |
|
|
Print information about containers. |
|
|
View container, image, volume, network, or pod configuration files. |
|
|
Download an image from a registry. |
|
|
Copy files or directories between a container and the local file system. |
|
|
Execute a command in a running container. |
|
|
Delete one or more containers. |
|
|
Delete one or more images. |
|
|
Search for an image in a registry. |
You can access more commands about Podman through this link.
What is a pod?
Podman pods allow you to manage multiple containers as a single unit by bringing them together. Podman pods are a group of one or more containers that share the same network namespace and file system. This means that containers within a pod can communicate with each other as if they were running on the same machine and can access the same files and directories.
One advantage of using pods is that they provide a more isolated environment compared to running containers individually. When you run containers individually, they share the same network namespace, enabling direct communication between them. However, within a pod, each container has its own network namespace, providing additional isolation.
Podman pods also provide a way to manage the lifecycle of a group of containers. You can start, stop, and delete a pod as a single unit, making it easier to manage complex applications that require multiple containers to work together.
Overall, Podman pods are a useful tool for managing container groups that work together in a more isolated and organized manner.

Fig.2.[2]
Infra Container: It maintains the namespaces associated with the pod and allows Podman to link other containers to the pod.
Container(s): These are regular containers where your application resides. They can communicate with other containers within the pod using the shared network namespace.
Some Podman pod commands include:
|
Command |
Description |
|
|
Creates a new pod. |
|
|
Deletes a pod. |
|
|
Used to remove unused pods. |
|
|
Starts a pod. |
|
|
Stops a pod. |
|
|
Restarts a pod. |
|
|
Pauses a pod. |
|
|
Resumes a paused pod. |
|
|
Stops all processes in a pod by sending the SIGKILL signal to all running containers in the specified pod. |
|
|
Displays the processes within a pod. |
|
|
Displays the logs of a pod. |
|
|
Displays the details of a pod. |
|
|
Displays the resource usage statistics of a pod. |
Running Rootless Pods:
1. To control potential rootless containers and pods, use the --pod option to display the identity and name of the pod to which the containers belong:
2. Check for existing pods:
Ø podman ps -a --pod
Ø podman pod ps

3. Let's create a pod named "my-pod" where the port 80 inside the pod is forwarded to port 8080 on the host machine:
4. Check the existing pods and containers again:
Ø podman pod create --name my-pod -p 8080:80
Ø podman pod ps

The infra container created with my-pod should now be listed by default. Additionally, the published ports of the pod are listed, and it is verified that port 80 is being forwarded to port 8080.
5. Add a container named "mariadb" to the my-pod pod with the following parameters and environment variables:
• Set with --restart=always option.
• Set MYSQL_ROOT_PASSWORD as dbpass.
• Set MYSQL_DATABASE as my.
• Set MYSQL_USER as wordpress.
• Set MYSQL_PASSWORD as mypass
Ø podman run -d --restart=always --pod=my-pod -e MYSQL_ROOT_PASSWORD= “dbpass” -e MYSQL_DATABASE=”my” -e MYSQL_USER=”wordpress” -e MYSQL_PASSWORD=”mypass” –name=my-db mariadb

6. Add a Wordpress container named "my-web" to the my-pod pod with the following parameters and environment variables:
• Set with --restart=always option.
• Set WORDPRESS_DB_NAME as my.
• Set WORDPRESS_DB_USER as wordpress.
• Set WORDPRESS_DB_PASSWORD as mypass.
• Set WORDPRESS_DB_HOST as 127.0.0.1.
Ø podman run -d --restart=always --pod=my-pod -e WORDPRESS_DB_NAME = “my” -e WORDPRESS_DB_USER =” wordpress” -e WORDPRESS_DB_PASSWORD =”mypass” -e WORDPRESS_DB_HOST =”127.0.0.1” –name=my-web wordpress

7. Verify that the web server on the Wordpress server can be accessed through the published ports using curl, and ensure it is functioning properly:
Ø curl -s http://localhost:8080
(Nothing will be returned)
8. Check the exit code immediately:
Ø echo $?
![]()
9. We can use the "podman pod stop" command to stop the pod and all the containers within it.
![]()
The My-Pod pod and its containers, including My-Web, My-DB, and infra containers, should be listed or stopped as output.
10. Use the "podman pod start" command to restart the pod and its containers.

11. Use the "podman pod restart" command to restart the pod and its containers:
The my-pod pod and its my-web, my-db, and infra containers should all be listed as running or active

Podman vs. Docker

fig.3.(Podman Tutorial For Beginners: Step By Step Guides (devopscube.com))
Docker is a tool that enables the creation and usage of Linux containers, which is a form of containerization technology. The key difference lies in Podman's daemonless architecture, which sets it apart from Docker. Podman containers are always rootless, whereas Docker has recently added a rootless mode as an additional configuration to its daemon. Docker is a single tool for container creation and management, while related tools like Podman and Buildah are more specialized and customizable for specific aspects of containerization to cater to different needs.
Podman serves as a powerful alternative to Docker and can be used alongside it. Users can easily switch between Docker and Podman by changing aliases, such as aliasing docker to podman and vice versa. Additionally, an RPM called "podman-docker" can be used to ease the transition to Podman for environments that rely on the 'docker' command. It allows placing 'docker' in the system application PATH and facilitates the transition to Podman while still invoking Docker. The CLI of Podman is similar to the Docker Container Engine, making it highly likely for users familiar with one to succeed with the other.
Commands performed in Docker can also be executed in Podman. Furthermore, Podman can work with files named Dockerfile and Containerfile.
Ø 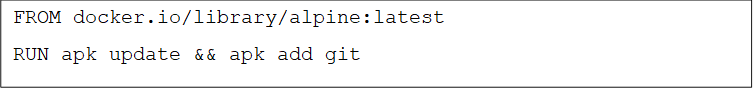 vim Dockerfile
vim Dockerfile
Ø pod build -t my-git-image
At the end of the command, we specify the directory where the Dockerfile is located.

Ø podman run -it my-git-image

Podman, Buildah, and Skopeo
Podman, Buildah, and Skopeo are three different tools used for containerization. These tools embrace a modular approach to containerization and provide a flexible and lightweight environment when used together.
Buildah is a tool used for building and managing container images. It uses a configuration file called Podmanfile instead of Dockerfile, and can create images from scratch or use an existing image as a starting point. Buildah also allows configuring images using a series of commands instead of a Dockerfile.
Skopeo is a tool used for copying and moving container images between different sources. It can be used to transition between images stored in different repositories, such as docker.io or quay.io. [1]
Podman is a tool used for running containers and is considered an alternative to Docker. It provides a similar command-line interface to Docker but employs a different architecture. Podman has a daemonless architecture and runs in a rootless mode. It also utilizes an OCI runtime called runC.
Red Hat likens this relationship to a Swiss Army Knife, with Podman being interpreted as the largest blade.
You can refer to this link to examine the relationship between Podman and Buildah.
Podman Desktop
Podman Desktop is a GUI tool for managing Podman containers. It is available for Windows, macOS, and Linux systems. Podman Desktop makes it easy to view, start, stop, and manage containers through its graphical interface. It also supports many features, such as running and monitoring multiple containers simultaneously. Additionally, you can obtain detailed logs to ensure that your application is running as expected.
For users who are familiar with using Docker Desktop and prefer a GUI experience, Podman provides a solution in this regard. That's why we wanted to touch upon this topic.

Fig.4.(https://developers.redhat.com/articles/2022/10/24/podman-expands-desktop)
You can download and install Podman Desktop from this link.
Conclusions and Future Studies
In conclusion, Podman is a powerful and flexible container engine that offers several advantages compared to other container engines like Docker. Its daemon-less architecture makes it more secure and user-friendly, while the support for rootless containers provides more flexibility in managing container environments.
The ability of Podman to run containers as normal processes of the host system allows for easier integration with existing system management tools and workflows, and its Kubernetes support makes it a suitable choice for deploying container-based applications in a Kubernetes environment.
In our future articles, we will delve deeper into Podman, exploring its networking and monitoring aspects, as well as discussing the container tools mentioned briefly above (skopeo, buildah) in more detail.
Resources
1.Red Hat. (2021). What is Podman? Erişim tarihi: Mart 17, 2023, from https://www.redhat.com/en/topics/containers/what-is-podman#how-does-podman-manage-containers
2. ACloudGuru. (n.d.). Hands-On with Podman Containers. Erişim tarihi: Mart 17, 2023, from https://learn.acloud.guru/course/hands-on-with-podman-containers/dashboard
3.Podman documentation. (n.d.). Erişim tarihi: Mart 17, 2023, from https://docs.podman.io/en/latest/
4.Red Hat. (n.d.). podman(1) - Linux man page. Erişim tarihi: Mart 17, 2023, from https://www.systutorials.com/docs/linux/man/1-podman/
5. Red Hat. (n.d.). Managing containers with Podman. Erişim tarihi: Mart 17, 2023, from https://rol.redhat.com/rol/app/courses/rh134-9.0/pages/ch11